If you are here, I suppose you know that Netcat (NC) is an utility which reads and writes data across network connections, using TCP or UDP transport. Nothing more, nothing less.
Let’s see some exemples of use.
First of all let’s read the help output:
[v1.11 NT www.vulnwatch.org/netcat/]
connect to somewhere: nc [-options] hostname port[s] [ports] ...
listen for inbound: nc -l -p port [options] [hostname] [port]
options:
-d detach from console, background mode
-e prog inbound program to exec [dangerous!!]
-g gateway source-routing hop point[s], up to 8
-G num source-routing pointer: 4, 8, 12, ...
-h this cruft
-i secs delay interval for lines sent, ports scanned
-l listen mode, for inbound connects
-L listen harder, re-listen on socket close
-n numeric-only IP addresses, no DNS
-o file hex dump of traffic
-p port local port number
-r randomize local and remote ports
-s addr local source address
-t answer TELNET negotiation
-u UDP mode
-v verbose [use twice to be more verbose]
-w secs timeout for connects and final net reads
-z zero-I/O mode [used for scanning]
port numbers can be individual or ranges: m-n [inclusive]
This is the Windows version of Netcat, but options are similar also in Linux. The version I found for MacOS don’t have the -e option, but you can recompile it to enable this option or use some workaround as I will explain.
First try: open two command windows in the same machine. In the first window start a service that listens on a specific port using Netcat (this is called listener)
If you have a look at the network connection of your machine, using the command netstat -na, you will find a listening connection on port 4444 tcp 0.0.0.0:4444 LISTEN
In the second window use NC as a client and connect to localhost on port 4444
Hit enter and you establish a simple connection with NC, but what is this?
Essentially is a simple chat. If in window 1 you write something it will redirect to windows 2 and vice versa.
So NC is a program that allows you to communicate using TCP or UDP protocols and you can use it whether as a client or as a server. TCP/UDP connections are more useful than a simple chat: you can use NC to test if a remote port is open, to grab information about a service listening on a remote PC (the banner) and to connect to this service; otherwise you can use it to redirect text, request html page, and, last but not least, remotely admin a PC.
Lets try NC to pass simple text file. This time I will use Linux because of its more simple command shell, but you can implement the same thing on Windows.
So, I try to pass text file starting the folowing listener
…and than connect
This can be useful to create or modify remotly config file as this:
…or simply add something to your TODO list
And now let’s transfer a file (note the -w option used to end connection and to unlock the file transferred):
Well, NC can be used to connect to listeners. If there is a service listening on some TCP/UDP port you can try to connect, and sometimes even interact with it:
220 (vsFTPd 2.3.5)
USER user-one
331 Please specify the password.
PASS ******
230 Login successful.
In some other case NC isn’t able to interact, but can be useful to grub banner and find what kind of service is listening. Look at the following command: you find a OpenSSH server on non-standard tcp port 2201.
localhost [127.0.0.1] 2201 (?) open
SSH-2.0-OpenSSH_6.0p1 Debian-4
Protocol mismatch.
You can implement this idea using -z option and transfotm NC in a port scanner. You will also like to specify port range.
localhost [127.0.0.1] 2201 (?) open
localhost [127.0.0.1] 1111 (?) open
localhost [127.0.0.1] 80 (http) open
localhost [127.0.0.1] 21 (ftp) open
If you use the -o option you can dump all hex traffic:
localhost [127.0.0.1] 4444 (?) open
hello
my password is ****** yes six asterisks
^C
root@kali:~# cat /tmp/log.txt
< 00000000 68 65 6c 6c 6f 0a # hello.
> 00000000 6d 79 20 70 61 73 73 77 6f 72 64 20 69 73 20 2a # my password is *
> 00000010 2a 2a 2a 2a 2a 20 79 65 73 20 73 69 78 20 61 73 # ***** yes six as
> 00000020 74 65 72 69 73 6b 73 0a # terisks.
Let’s now talk about remote admin. You can use -e option to execute programs, in this case cmd.exe or /bin/bash.
So, start a listener in one terminal window:
listening on [any] 4444 ...
…and connect to it using a second command shell:
Microsoft Windows [Versione 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. Tutti i diritti riservati.
c:\>hostname
hostname
windows-pc01
c:\FAKE_Path>
You can also set the listener without -e option and use it on the client. The result will be a remore shell of the client on the machine with the listener.
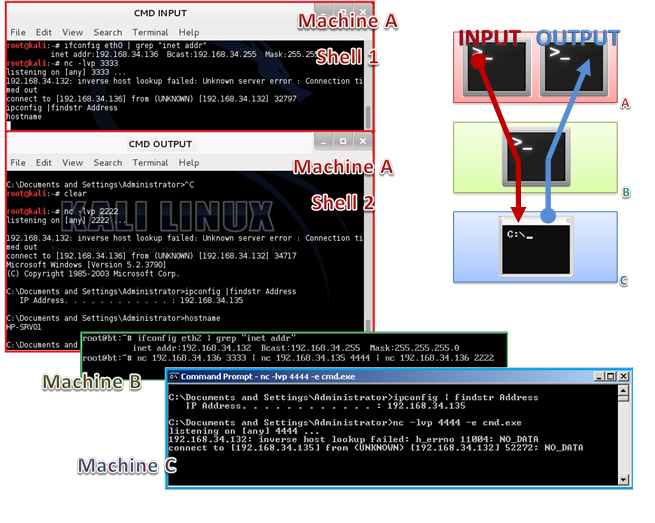
Of course you can put together text/command redirection and command execution. Look at the immage below.
We have 3 PCs: machine A and B are Linux, machine C is Windows. Let’s start 2 listeners in two different windows in Machine A; then one listener with -e option on the Windows PC. When all listeners are ready let’s put all together running the 3 clients from Machine B. we wait some seconds and … TA-DAAA! In the Machine A we have a remote shell of the Windows system. Note that pipeling in Machine B has as effect that, in Machine A, you write the command in shell 1 and read output in shell 2.
This sound like a remote shell using a proxy…
Now let’s try the MacOS Netcat version. The only preconpiled version I found is an old one, non supporting “executing command” option (-e). Although we can compile a surce code that incluce the option we want, we can also modify the previous exemple to make command execution working.
Start on a machine (IP=10.0.0.1) two shell each one with a listener.
In the remote Mac you have to admin, start a pipeling as this:
Great! You have a remote shell of your Mac.
That’s why netcat is so important. It is so simple and so powerful that you can use it either for basic connection tests or in a complex environment, but the most important thing is that is cross-platform, single file and stand-alone program. It can also be used to implement many complex environment as proxy, sniffer, logger, secure chat, debbugger, fuzzer. You can even use it backup your disk partition on another PC (how to copy compressed drive image over network).
Nowadays there are many Netcat clones, some of these use encryption or implement the remote command execution and the use of passwords; you can easely find it googling.
Obviously not always it work as we’ll wish. One exemple overall: when we start a remote shell using NC with -e option we don’t have a FULL interactive command prompt, but a NON interactive one. To better understand try this: connect to an FTP server using NC directly. You will prompt to insert USER and then PASS and everything works, but if you try to connect to the FTP server from a remote shell (using NC aswell) you will promt to insert USER and, when you hit enter, your session will hang.
In this post you can find some solutions to reach a full interactive shell from a NC non interactive shell.
You can find more info on NetCat Home Page.